Kafka in the Cloud: Why it’s 10x better with Confluent | Find out more
Enabling SIEM Architects to Augment and Optimize Cybersecurity Solutions
Today, SIEM architects are tasked with turning disparate, legacy cybersecurity solutions into an integrated IT platform capable of analyzing and acting on security data from various sources. Confluent’s solution for cybersecurity augments your existing SIEM and SOAR solutions to deliver contextually rich data, automate and orchestrate threat detection, reduce false positives, and transform the way your organization detects, analyzes, and responds to threats and cyber attacks in real time.

"As cyber threats continuously grow in sophistication and frequency, companies need to quickly acclimate to effectively detect, respond, and protect their environments. At Intel, we’ve addressed this need by implementing a modern, scalable Cyber Intelligence Platform (CIP) based on Splunk and Confluent. We believe that CIP positions us for the best defense against cyber threats well into the future.“
Brent Conran, Chief Information Security Officer
Maximize the Value of your SIEM Platforms
SIEM is driven by three factors - scale, speed and cost. The growing diversity, velocity and exponential volume of security data have rendered legacy SIEM technologies incapable of dealing with the current requirements of Information Security (InfoSec) teams and Security Operations Centers (SOCs). Most organizations now realize that they need to be more independent from any given SIEM vendor, and have the ability to leverage multiple tools and analytic destinations.
Combine the best real-time streaming data infrastructure and your cybersecurity platforms to break down silos and deliver contextually rich data to be more situationally aware. With Confluent, you can gain world-class data ingestion and real-time analytics while optimizing for cost and scale.
How Confluent Helps you Optimize your SIEM
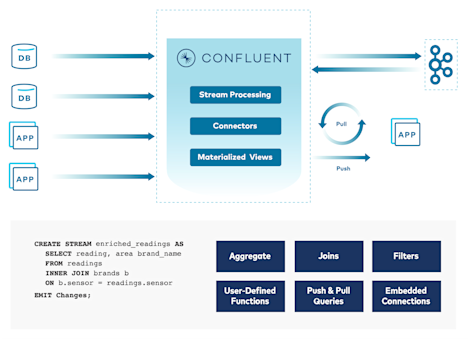
Move from Batch to Real-time at Stream Scale
Design a next-gen cybersecurity data infrastructure with a real-time SIEM pipeline.
- Ingest, aggregate, and store security event and sensor data with over 120 pre-built connectors like Splunk, Elasticsearch, SNMP, Syslog, AWS Cloudwatch and more.
- Handle trillions of messages per day and petabytes of data effortlessly and process them in milliseconds.
Improve Data Quality and Reduce Time to Threat Detection and Resolution
Curate, enrich and normalize data to enable threat detection and data engineering at the edge or point of collection for contextually rich insights.
- Use sophisticated stream processing and Single Message Transforms to aid richer threat and anomaly detection.
- Filter noisy data by suppressing and masking events that do not contribute to incident detection and investigation.
- Push processing to edge and point of collection decreasing latency for faster insights.
- Train and bring ML/AI models faster to production faster to aid with richer real-time threat detection.
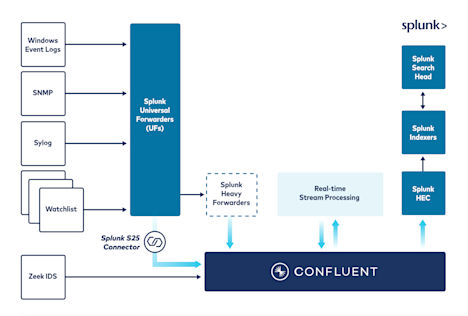
Reduce Data Indexing, Analysis and Storage Costs
Mitigate the impact of increasing data storage and analysis costs that force tradeoffs between cost, flexibility and visibility.
- Reduce ingest and index volume and overall licensing costs that come with consumption-rate, volume-based pricing.
- Reduce the need for proprietary intermediary forwarders to reduce overall operating expenses with Splunk S2S connector.
- Route your data to cost-effective destination with tiered storage and connectors to cloud storage infrastructure like Amazon S3, Google Cloud Storage, Azure Blob storage, Snowflake and HBase.
- Filter and aggregate prior to network egress and ingress reducing infrastructure and cloud costs.
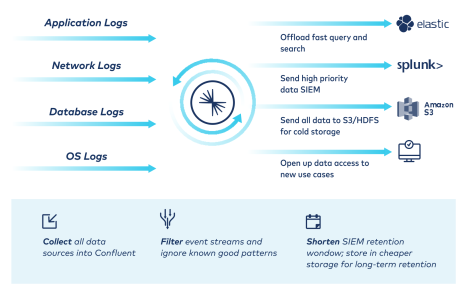
Achieve Freedom of Choice
Gain unprecedented flexibility to choose your own data destiny, regardless or source or destination, eliminate lock-in and enable best of breed.
- Make your data portable by easily integrating and sharing data from any source to any destination, in any environment.
- Seamlessly migrate from old-school SIEM tools to next-gen solutions without worrying about dropping or losing data.
- Enable access to best of breed tools to strengthen cybersecurity and democratize data access.
Simplified Architecture, Advanced Functionalities
Broad Connectivity
Utilize a broad array of source and sink pre-built connectors to easily connect and move data in and out of popular systems.
Advanced Processing
Transform and enrich your data in-stream by continuously processing them with Apache Flink and Single Message Transforms.
Infinite Retention
Retain and store data for extended periods of time for analytic engines that may want to look at months of events with infinite storage.
Industry-leading Security
Minimize the risk of security breaches and downtime with RBAC, Audit Logs, and Secret Protection.
Flexible Architecture
Build a persistent bridge to enable real-time data interoperability everywhere, on-prem, in the cloud or on the edge.
Future-proof Design
Design a flexible architecture to integrate new sources or targets by decoupling point-to-point integrations.
Observability Solutions Built on Kafka

Datadog
Datadog uses Kafka as their underlying messaging technology, ingesting data across trillions of data points per day.

New Relic
New Relic uses Kafka to easily build real-time monitoring and observability pipelines with real-time alerts.

SignalFX
SignalFX uses Kafka for modern monitoring and analytics that processes hundreds of thousands of messages per second.

Honeycomb
Honeycomb processes large influxes of event traffic by leveraging Kafka to safely publish and ingest messages between distributed systems.

Salesforce
Salesforce built an enterprise-ready, event-driven layer with Kakfa for delivery and ordering guarantees in a secure, multitenant system.

Microsoft
Microsoft Azure processes up to 30 million events per second and trillions of events per day using Kafka for data ingestion and streaming.
Additional Resources
Reference Architecture
Elastic and Confluent Technical Reference Architecture
Blog Post
Seamless SIEM: Osquery Event Log Aggregation
Intel Talk
Building a Modern, Scalable Cyber Intelligence Platform at Intel
Blog Post
How Confluent Can Help Optimize and Modernize Your SIEM for Better Cybersecurity
Learn About Other Confluent Solutions
Learn more about how Confluent's complete, fully managed event streaming platform is revolutionizing the way businesses achieve real-time data management, insights and analytics across a wide variety of use cases.